The Fleckpe Malware: Unveiling a Deceptive Trojan Targeting Google Play Store Users
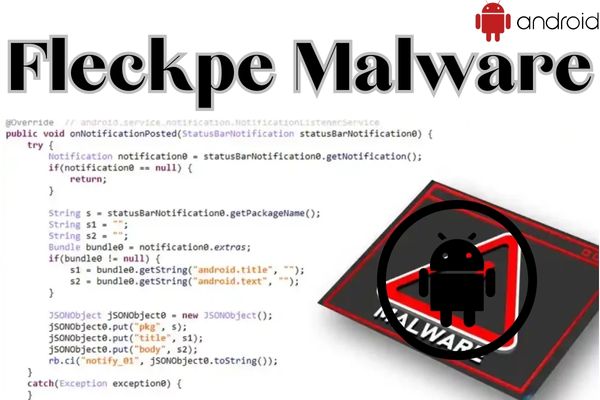
A new Android malware called Fleckpe malware has emerged as a major threat to users of the Google Play Store. Disguised as legitimate apps, Fleckpe has been installed over 620,000 times, spreading through various commonly available applications such as photo editing apps and smartphone wallpaper packs. This article sheds light on the nature of the Fleckpe malware, its alarming capabilities, and provides insights on how users can protect themselves from this deceptive Trojan.
Android Fleckpe Malware: Targeting Users of the Google Play Store
Malware in Disguise: The Fleckpe Infiltration:
Fleckpe, cleverly disguised within seemingly harmless apps, has managed to bypass security measures on the Google Play Store. Its presence was identified in 11 apps, which have since been removed, but there is a possibility that other undetected apps carrying the malware may still be in circulation.
Unauthorized Charges and Subscription Fraud:
The primary goal of Fleckpe is to generate unauthorized charges by subscribing users to premium services without their knowledge or consent. Victims only realize they have been charged when they discover unexpected fees for services they never intended to purchase. This subscription fraud is a significant concern, leading to financial losses and eroding user trust.
Sophisticated Operation and Stealthy Techniques:
Fleckpe operates discreetly, remaining undetected until users notice the unauthorized charges. The malware employs a malicious native library to establish contact with threat actors, sharing device information. The information is then used to initiate a paid subscription process through an invisible web browser page, effectively siphoning money from unsuspecting users.
Targeted Regions and Potential Impact:
Although predominantly targeting users in Thailand, Fleckpe has also shown signs of targeting users in Poland, Malaysia, Indonesia, and Singapore. The malware’s widespread distribution and potential impact on a broad range of users highlight the urgent need for heightened security measures.
Rise of Subscription Trojans and Marketplace Vulnerabilities:
Fleckpe is the latest addition to the growing list of subscription Trojans, including the notorious Joker and Harley malware families. Scammers are increasingly exploiting official marketplaces like the Google Play Store to distribute their malicious creations. The sophistication of these Trojans allows them to evade detection for extended periods, bypassing anti-malware checks and compromising user security.
Protecting Against Fleckpe and Similar Malware:
While protecting against malware distributed through trusted marketplaces can be challenging, users can take proactive steps to enhance device security. It is crucial to exercise caution when downloading apps, even from the Google Play Store. Carefully review app privacy policies and permissions requested, and be wary of apps from unverified publishers or unknown sources.
Stay Updated:
Keep your device’s operating system, apps, and antivirus software up to date. Regular updates often include security patches that can help protect against known vulnerabilities.
Download from Trusted Sources:
Stick to official app stores like the Google Play Store, as they have security measures in place to detect and remove malicious apps. Avoid downloading apps from unverified sources or third-party app stores, as they pose a higher risk.
Read App Reviews and Ratings:
Before downloading an app, read user reviews and ratings to get insights into its reliability. Look out for any reported issues or suspicious activities mentioned by other users.
Check App Permissions:
Review the permissions an app requests during installation. Be cautious if an app asks for unnecessary permissions that seem unrelated to its functionality. If an app requests access to sensitive data or features without a valid reason, reconsider installing it.
Be Cautious with Personal Information:
Avoid providing unnecessary personal information to apps unless it is essential for their intended functionality. Be wary of apps that request excessive personal data or permissions that seem unrelated to their purpose.
Verify App Developer Information:
Research the app developer before downloading their app. Verify their reputation, history, and credibility. Stick to apps developed by reputable companies or developers with a track record of delivering trustworthy applications.
Use Reliable Mobile Security Software:
Install a reputable mobile security application that provides real-time protection against malware, scans downloaded apps for threats, and offers additional security features such as app permission monitoring and safe browsing.
Be Mindful of Phishing Attempts:
Be cautious of suspicious emails, messages, or links that prompt you to download apps outside of official app stores. Scammers often use phishing techniques to trick users into installing malware-infected apps.
Educate Yourself:
Stay informed about the latest threats, malware trends, and security best practices. Regularly seek reliable sources of information to stay up to date with potential risks and protective measures.
Report Suspicious Apps:
If you come across a suspicious app or suspect malware on your device, report it to the official app store or the appropriate authorities. Reporting helps in removing harmful apps from circulation and safeguarding other users.
FAQ
Q: What is the Fleckpe malware?
A: The Fleckpe malware is a deceptive Trojan that targets users of the Google Play Store. It disguises itself as legitimate apps and has been installed over 620,000 times.
Q: How does Fleckpe operate?
A: Fleckpe works by covertly subscribing users to premium services without their knowledge or consent. It initiates unauthorized charges, leaving victims surprised when they discover unexpected fees for services they never intended to purchase.
Q: How did Fleckpe infiltrate the Google Play Store?
A: Fleckpe managed to bypass security measures on the Google Play Store by masquerading within seemingly harmless apps. It was identified in 11 apps, which have since been removed, but there may be other undetected apps carrying the malware.
Q: What are the potential impacts of Fleckpe?
A: The primary impact of Fleckpe is financial, as users may experience losses due to unauthorized charges. Additionally, it erodes user trust in the Google Play Store and the overall app ecosystem.
Q: How does Fleckpe carry out subscription fraud?
A: Fleckpe loads a malicious native library that communicates with threat actors and shares device information. This information is used to initiate a paid subscription process through an invisible web browser page, allowing the malware to siphon money from users.
Q: Which regions are primarily targeted by Fleckpe?
A: Fleckpe primarily targets users in Thailand. However, signs of targeting users in Poland, Malaysia, Indonesia, and Singapore have also been found.
Q: How can users protect themselves against Fleckpe and similar malware?
A: Users should exercise caution when downloading apps, even from the Google Play Store. Reading privacy policies, carefully assessing app permissions, and avoiding apps from unverified publishers or unknown sources are recommended steps to enhance security.
Q: Are there any other notable malware similar to Fleckpe?
A: Yes, Fleckpe joins the ranks of other subscription Trojans like the Joker and Harley malware families, which have also exploited official marketplaces for their distribution.
Q: How can users report suspicious apps or malware to the Google Play Store?
A: Users can actively contribute to the detection and removal of suspicious apps by reporting them to the Google Play Store. This helps in maintaining a safer app environment for all users.
Q: What are the long-term implications of malware like Fleckpe?
A: The emergence of sophisticated malware like Fleckpe underscores the need for continuous security measures. Developers and marketplace operators must enhance their security protocols to prevent the infiltration of malicious apps, protecting users and preserving trust in the app ecosystem.
- 10 Essential Internet Safety Tips to Protect Your Online Presence
- Get Organized: Tech Tips for Managing Your Digital Life
- AI Tool for Google Dorks: How to Automate the Search for
Conclusion:
Fleckpe’s emergence as a deceptive Trojan targeting users on the Google Play Store serves as a stark reminder of the evolving threats in the digital landscape. Users must remain vigilant, adopt security best practices, and exercise caution when downloading and using apps. By staying informed and taking proactive measures, we can defend against the infiltration of malicious malware like Fleckpe and ensure a safer mobile ecosystem for all.







